
Amazon Inspectorの検出結果をAWS Security Hubを経由してメール通知する
この記事は公開されてから1年以上経過しています。情報が古い可能性がありますので、ご注意ください。
はじめに
本記事では、Amazon Inspectorの検出結果をAWS Security Hubを経由してメール通知する方法を解説します。
この設定を行うことで、重要なセキュリティアラートをリアルタイムで把握し、迅速に対応することが可能になります。
前提条件
- AWS Security Hubが有効化されていること
- メール通知用のAmazon SNSトピックが作成済みであること
Inspectorを有効化
- AWSマネジメントコンソールからInspectorサービスページに移動し、「Inspectorをアクティブ化」をクリックします。
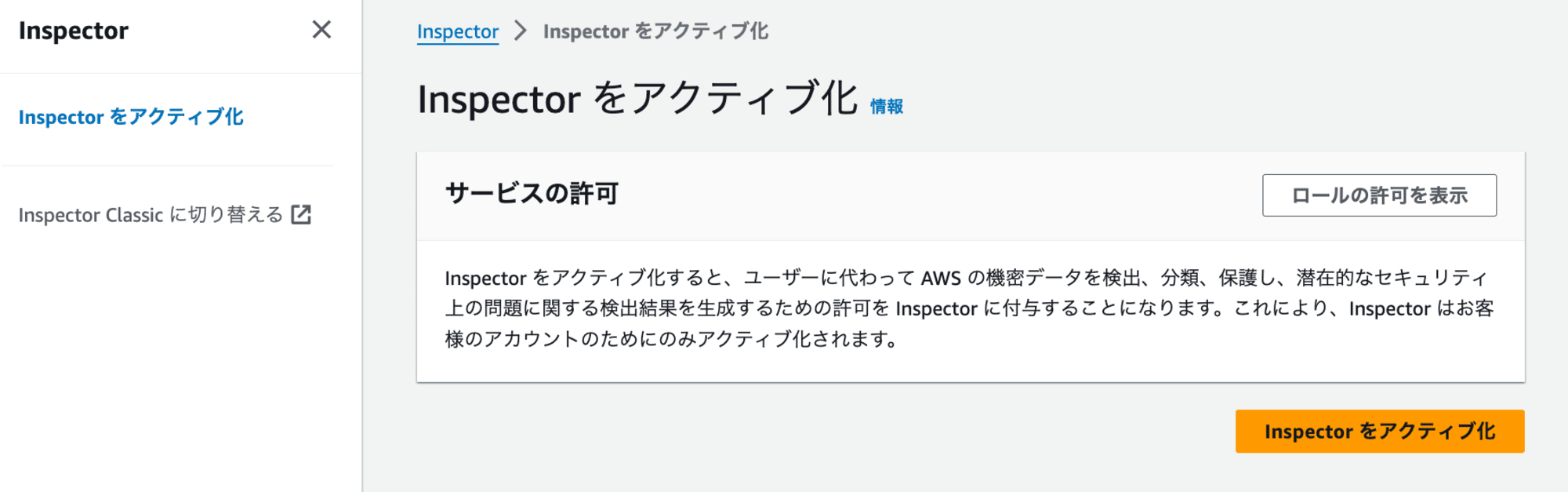
- 設定画面で、EC2、ECR、Lambdaのスキャンが有効になっていることを確認します。
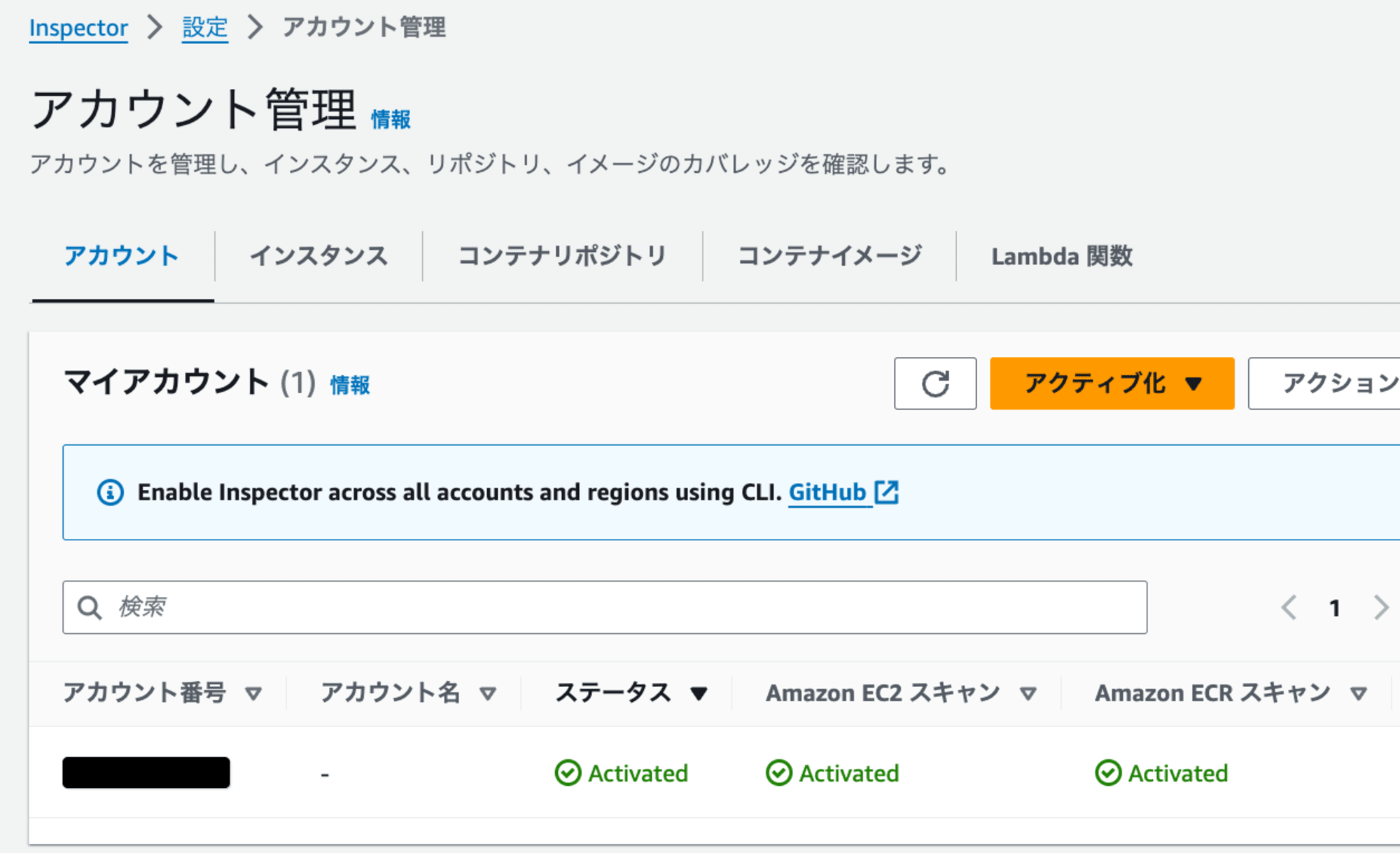
Security Hub統合
次に、InspectorがSecurity Hubと統合されているか確認します。
Security Hubサービスページに遷移し、以下の通り、有効化されていればよいです。
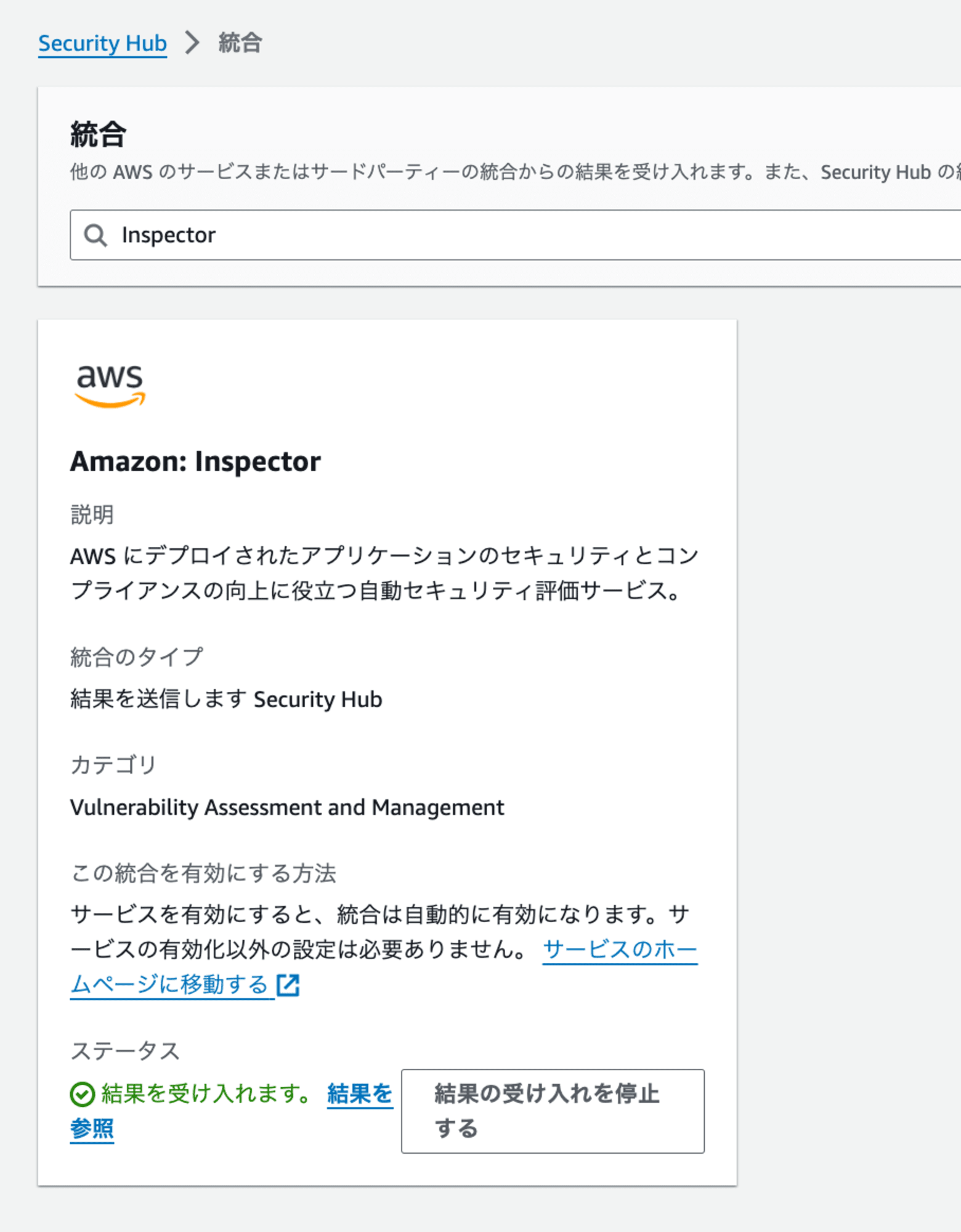
この統合が有効化されていることで、Inspectorの検出結果がSecurity Hubに自動的に送信されるようになります。
EventBridgeルール
次に、Security Hubに送られたInspectorの検出結果を基にメール通知を行うためのAmazon EventBridgeルールを作成します。このルールを適切に設定することで、重要度の高いセキュリティアラートのみを選別して通知することが可能になります。
以下の通りイベントパターンを設定して、重要度の高いInspectorの検出結果のみが通知されるようにします。
{
"source": ["aws.securityhub"],
"detail-type": ["Security Hub Findings - Imported"],
"detail": {
"findings": {
"ProductName": ["Inspector"],
"RecordState": ["ACTIVE"],
"Severity": {
"Label": ["HIGH", "CRITICAL"]
}
}
}
}
Amazon Inspector v2の検出結果のみを通知し、Amazon Inspector Classicの検出結果を除外したい場合は、以下のようにaws/inspector/ProductVersionを2に設定します。
{
"source": ["aws.securityhub"],
"detail-type": ["Security Hub Findings - Imported"],
"detail": {
"findings": {
"ProductName": ["Inspector"],
"ProductFields": {
"aws/inspector/ProductVersion": ["2"]
},
"RecordState": ["ACTIVE"],
"Severity": {
"Label": ["HIGH", "CRITICAL"]
}
}
}
}
ターゲットには、メール通知用のSNSトピックを選択します。
通知内容をカスタマイズするために入力パスを設定します。
この設定により、メール通知に含める具体的な情報を指定できます。
{
"AwsAccountId": "$.detail.findings[0].AwsAccountId",
"FirstObservedAt": "$.detail.findings[0].FirstObservedAt",
"LastObservedAt": "$.detail.findings[0].LastObservedAt",
"Region": "$.detail.findings[0].Resources[0].Region",
"ResourceId": "$.detail.findings[0].Resources[0].Id",
"ResourceType": "$.detail.findings[0].Resources[0].Type",
"SeverityLabel": "$.detail.findings[0].Severity.Label",
"Title": "$.detail.findings[0].Title"
}
以下の通り入力テンプレートを設定して、メール通知の具体的な内容と形式を定義します。
"Inspectorでセキュリティアラート"
"タイトル : <Title>"
"重要度 : <SeverityLabel>"
"アカウントID : <AwsAccountId>"
"リージョン : <Region>"
"リソースタイプ : <ResourceType>"
"リソースID : <ResourceId>"
"初回検出日時 : <FirstObservedAt>"
"最終検出日時 : <LastObservedAt>"
この設定により、Inspectorの検出結果が分かりやすい形式でメール通知されるようになります。
通知内容のテスト
設定した入力パスとテンプレートが正しく機能するか、通知内容のテストを行います。
このテストにより、実際の通知がどのように表示されるかを事前に確認できます。
筆者が用意した以下のECRスキャン結果のサンプルイベントをコピーし、サンプルイベント欄に記載します。
{
"version": "0",
"id": "b38fcac5-5d95-5cc3-f983-38bcdbed5ddd",
"detail-type": "Security Hub Findings - Imported",
"source": "aws.securityhub",
"account": "012345678901",
"time": "2024-09-27T04:58:52Z",
"region": "ap-northeast-1",
"resources": [
"arn:aws:securityhub:ap-northeast-1::product/aws/inspector/arn:aws:inspector2:ap-northeast-1:012345678901:finding/d7f4c00690caff2bf3288bbad69beb32"
],
"detail": {
"findings": [
{
"ProductArn": "arn:aws:securityhub:ap-northeast-1::product/aws/inspector",
"Types": ["Software and Configuration Checks/Vulnerabilities/CVE"],
"Description": "In MIT Kerberos 5 (aka krb5) before 1.21.3, an attacker can modify the plaintext Extra Count field of a confidential GSS krb5 wrap token, causing the unwrapped token to appear truncated to the application.",
"ProductName": "Inspector",
"FirstObservedAt": "2024-09-27T04:58:16.025Z",
"CreatedAt": "2024-09-27T04:58:16.025Z",
"LastObservedAt": "2024-09-27T04:58:16.025Z",
"Vulnerabilities": [
{
"ReferenceUrls": [
"https://www.cve.org/CVERecord?id=CVE-2024-37370",
"https://web.mit.edu/kerberos/www/advisories/",
"https://ubuntu.com/security/notices/USN-6947-1"
],
"Cvss": [
{
"Version": "3.1",
"BaseScore": 7.5,
"BaseVector": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N",
"Source": "UBUNTU_CVE"
},
{
"Version": "3.1",
"BaseScore": 7.5,
"BaseVector": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N",
"Source": "NVD"
},
{
"Version": "3.1",
"BaseVector": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N",
"BaseScore": 7.5,
"Source": "UBUNTU_CVE"
}
],
"FixAvailable": "YES",
"ExploitAvailable": "NO",
"VulnerablePackages": [
{
"Architecture": "AMD64",
"PackageManager": "OS",
"Version": "1.16",
"Epoch": "0",
"SourceLayerHash": "sha256:53fb22a46888376bf5f4fef0fe8cff28b2dd3e3ea6697a1d6803562f9e8ddf4f",
"FixedInVersion": "0:1.16-2ubuntu0.4+esm2",
"Remediation": "apt-get update && apt-get upgrade",
"Release": "2ubuntu0.4",
"Name": "libk5crypto3"
},
{
"Architecture": "AMD64",
"PackageManager": "OS",
"Version": "1.16",
"Epoch": "0",
"SourceLayerHash": "sha256:53fb22a46888376bf5f4fef0fe8cff28b2dd3e3ea6697a1d6803562f9e8ddf4f",
"FixedInVersion": "0:1.16-2ubuntu0.4+esm2",
"Remediation": "apt-get update && apt-get upgrade",
"Release": "2ubuntu0.4",
"Name": "libkrb5support0"
},
{
"Architecture": "AMD64",
"PackageManager": "OS",
"Version": "1.16",
"Epoch": "0",
"SourceLayerHash": "sha256:53fb22a46888376bf5f4fef0fe8cff28b2dd3e3ea6697a1d6803562f9e8ddf4f",
"FixedInVersion": "0:1.16-2ubuntu0.4+esm2",
"Remediation": "apt-get update && apt-get upgrade",
"Release": "2ubuntu0.4",
"Name": "libkrb5-3"
},
{
"Architecture": "AMD64",
"PackageManager": "OS",
"Version": "1.16",
"Epoch": "0",
"SourceLayerHash": "sha256:53fb22a46888376bf5f4fef0fe8cff28b2dd3e3ea6697a1d6803562f9e8ddf4f",
"FixedInVersion": "0:1.16-2ubuntu0.4+esm2",
"Remediation": "apt-get update && apt-get upgrade",
"Release": "2ubuntu0.4",
"Name": "libgssapi-krb5-2"
}
],
"EpssScore": 8.7e-4,
"Id": "CVE-2024-37370",
"RelatedVulnerabilities": ["USN-6947-1"],
"Vendor": {
"VendorCreatedAt": "2024-06-28T22:15:00.000Z",
"VendorSeverity": "medium",
"Url": "https://people.canonical.com/~ubuntu-security/cve/2024/CVE-2024-37370.html",
"Name": "UBUNTU_CVE"
}
}
],
"CompanyName": "Amazon",
"FindingProviderFields": {
"Types": ["Software and Configuration Checks/Vulnerabilities/CVE"],
"Severity": { "Normalized": 70, "Label": "HIGH" }
},
"ProductFields": {
"aws/inspector/ProductVersion": "2",
"aws/inspector/FindingStatus": "ACTIVE",
"aws/inspector/inspectorScore": "7.5",
"aws/inspector/resources/1/resourceDetails/awsEcrContainerImageDetails/platform": "UBUNTU_18_04",
"aws/inspector/packageVulnerabilityDetails/vulnerablePackages/sourceLayerHashes": "sha256:53fb22a46888376bf5f4fef0fe8cff28b2dd3e3ea6697a1d6803562f9e8ddf4f,sha256:53fb22a46888376bf5f4fef0fe8cff28b2dd3e3ea6697a1d6803562f9e8ddf4f,sha256:53fb22a46888376bf5f4fef0fe8cff28b2dd3e3ea6697a1d6803562f9e8ddf4f,sha256:53fb22a46888376bf5f4fef0fe8cff28b2dd3e3ea6697a1d6803562f9e8ddf4f",
"aws/securityhub/FindingId": "arn:aws:securityhub:ap-northeast-1::product/aws/inspector/arn:aws:inspector2:ap-northeast-1:012345678901:finding/d7f4c00690caff2bf3288bbad69beb32",
"aws/securityhub/ProductName": "Inspector",
"aws/securityhub/CompanyName": "Amazon"
},
"Remediation": {
"Recommendation": {
"Text": "Remediation is available. Please refer to the Fixed version in the vulnerability details section above.For detailed remediation guidance for each of the affected packages, refer to the vulnerabilities section of the detailed finding JSON."
}
},
"SchemaVersion": "2018-10-08",
"GeneratorId": "AWSInspector",
"RecordState": "ACTIVE",
"Title": "CVE-2024-37370 - libk5crypto3, libkrb5support0 and 2 more",
"Workflow": { "Status": "NEW" },
"Severity": { "Normalized": 70, "Label": "HIGH" },
"UpdatedAt": "2024-09-27T04:58:16.025Z",
"WorkflowState": "NEW",
"AwsAccountId": "012345678901",
"Region": "ap-northeast-1",
"Id": "arn:aws:inspector2:ap-northeast-1:012345678901:finding/d7f4c00690caff2bf3288bbad69beb32",
"Resources": [
{
"Partition": "aws",
"Type": "AwsEcrContainerImage",
"Details": {
"AwsEcrContainerImage": {
"Architecture": "amd64",
"ImageDigest": "sha256:3ee66704d2e9b9f64beaa0c8a61b3e824198fe57b1173a2383040d10710bfe38",
"RegistryId": "012345678901",
"RepositoryName": "hirai-poc-app-repo",
"ImagePublishedAt": "2024-09-27T04:57:39.000Z",
"ImageTags": ["latest"]
}
},
"Region": "ap-northeast-1",
"Id": "arn:aws:ecr:ap-northeast-1:012345678901:repository/hirai-poc-app-repo/sha256:3ee66704d2e9b9f64beaa0c8a61b3e824198fe57b1173a2383040d10710bfe38"
}
],
"ProcessedAt": "2024-09-27T04:58:49.605Z"
}
]
}
}
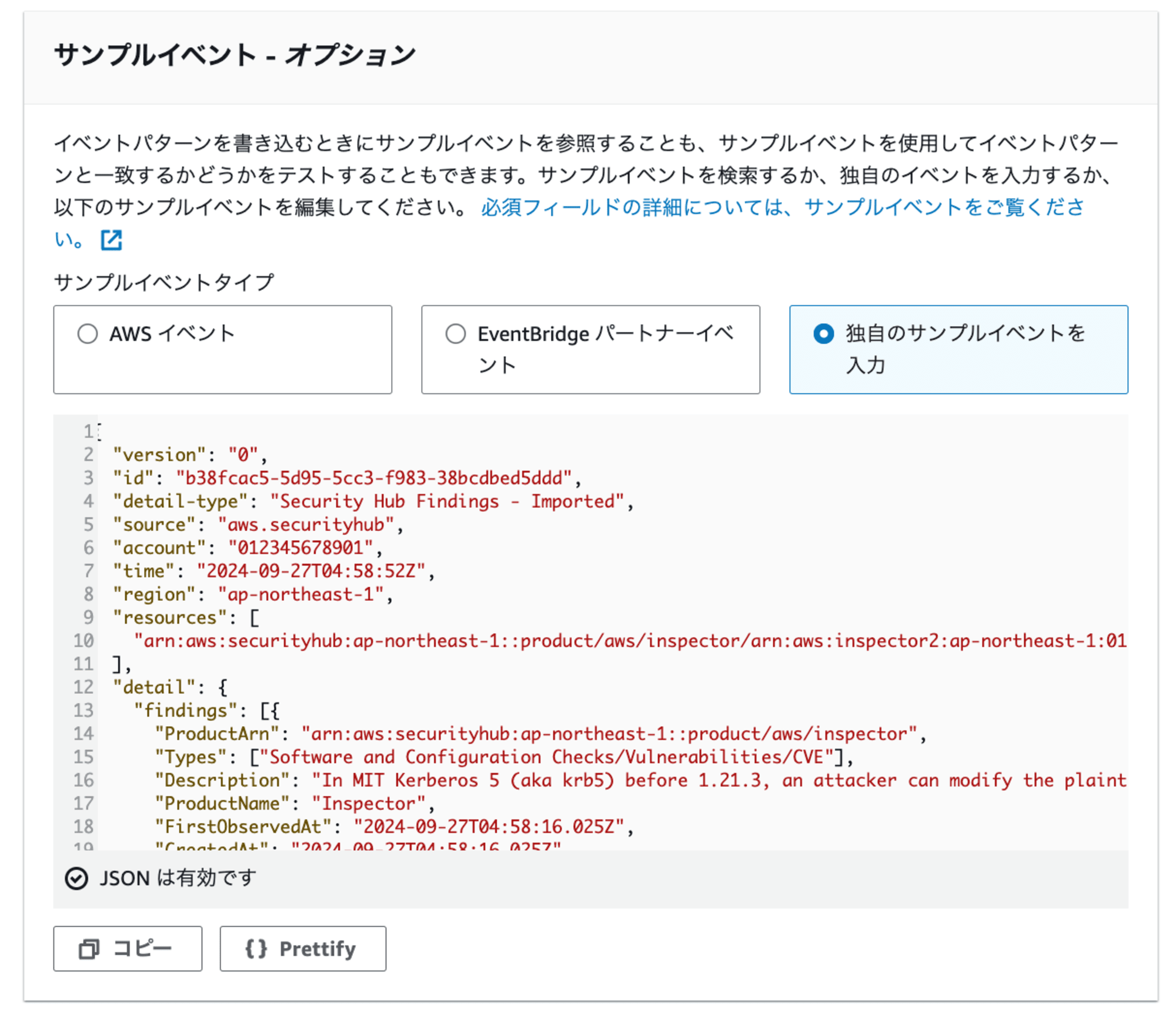
[出力を生成]で、メールでの実際の通知内容が確認できます。
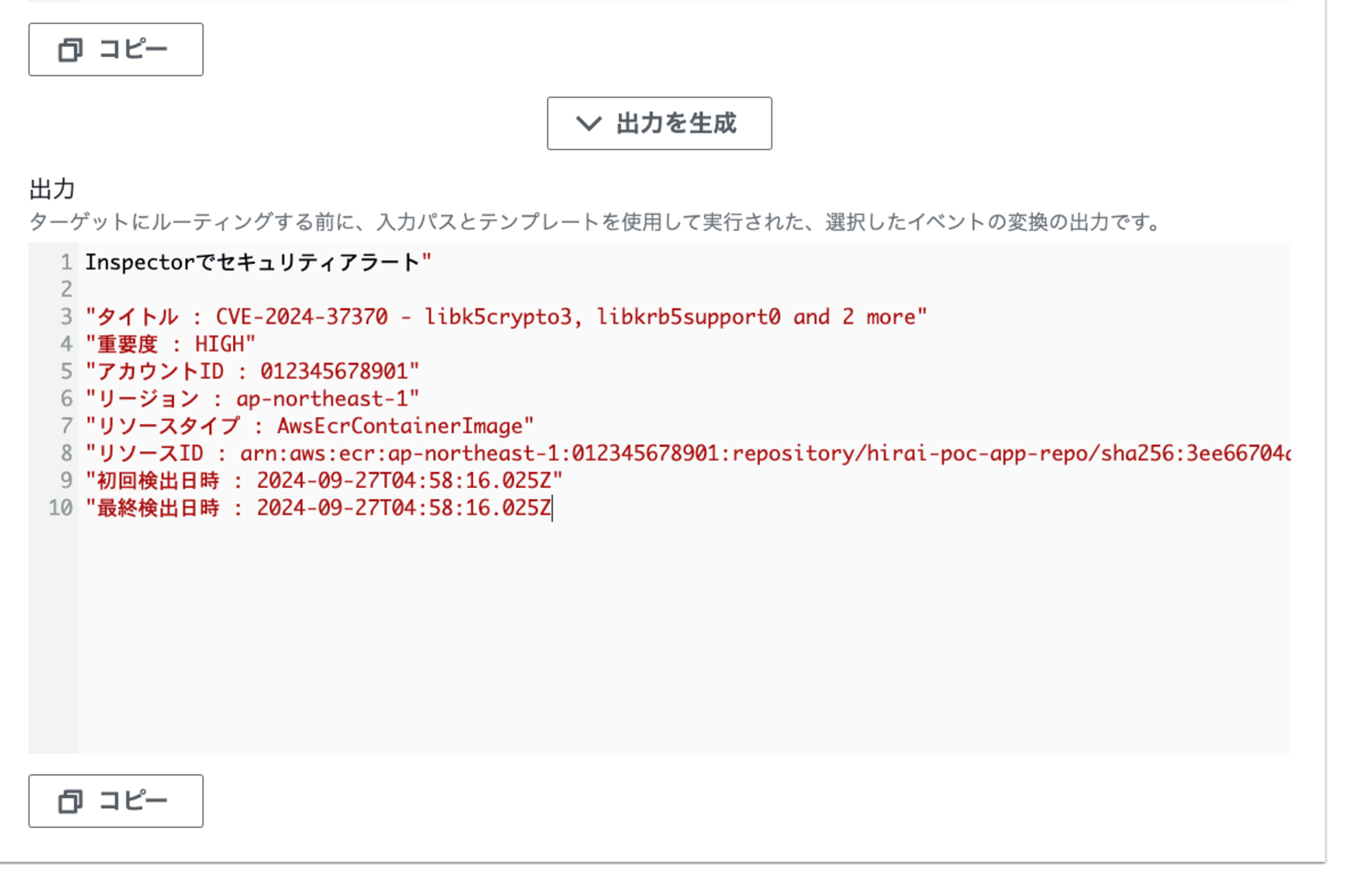
通知内容を修正したい場合、入力パスやテンプレートを修正します。
ちなみに、Amazon InspectorからAWS Security Hubを経由してAmazon EventBridgeに送信される完全なイベントサンプルは、現在のAWSの公式ドキュメントには記載されていません。
ただし、部分的なイベントサンプルは、以下のAWS公式ドキュメントで確認することができます。
試してみる
設定が完了したら、実際のInspectorの検出結果に基づいてメール通知が正しく機能するか確認します。
メール通知されました。
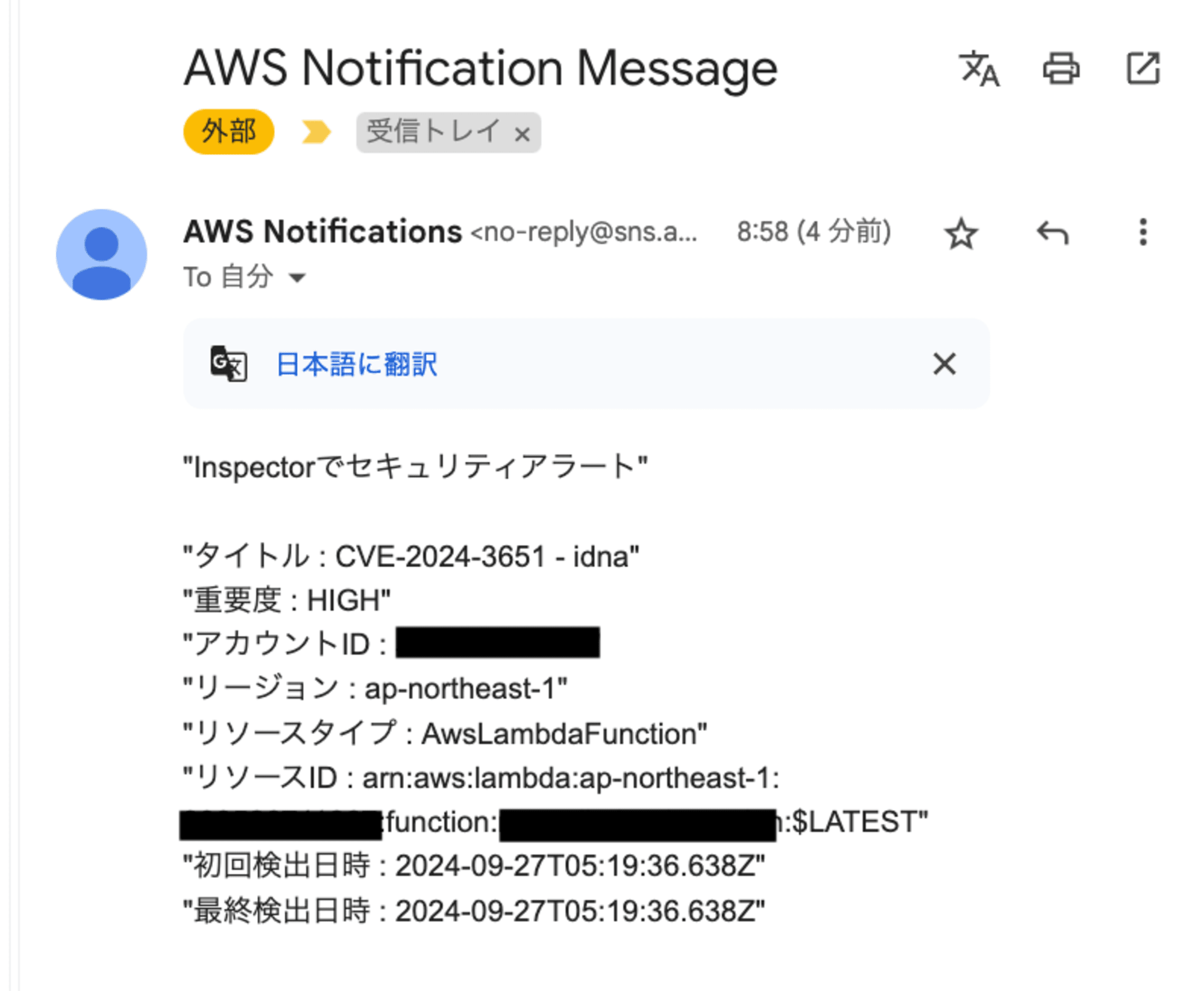
実際にSecurity Hubに送信されたイベント内容は以下の通りです。
{
"version": "0",
"id": "1dfae453-0bf2-9040-c541-045e1071e8de",
"detail-type": "Security Hub Findings - Imported",
"source": "aws.securityhub",
"account": "012345678901",
"time": "2024-09-27T05:19:57Z",
"region": "ap-northeast-1",
"resources": [
"arn:aws:securityhub:ap-northeast-1::product/aws/inspector/arn:aws:inspector2:ap-northeast-1:012345678901:finding/c33c6e60a31f11cd71bdb927268d8afe"
],
"detail": {
"findings": [
{
"ProductArn": "arn:aws:securityhub:ap-northeast-1::product/aws/inspector",
"Types": ["Software and Configuration Checks/Vulnerabilities/CVE"],
"Description": "A vulnerability was identified in the kjd/idna library, specifically within the `idna.encode()` function, affecting version 3.6. The issue arises from the function's handling of crafted input strings, which can lead to quadratic complexity and consequently, a denial of service condition. This vulnerability is triggered by a crafted input that causes the `idna.encode()` function to process the input with considerable computational load, significantly increasing the processing time in a quadratic manner relative to the input size.",
"ProductName": "Inspector",
"FirstObservedAt": "2024-09-27T05:19:36.638Z",
"CreatedAt": "2024-09-27T05:19:36.638Z",
"LastObservedAt": "2024-09-27T05:19:36.638Z",
"Vulnerabilities": [
{
"Cvss": [
{
"Version": "3.1",
"BaseScore": 7.5,
"BaseVector": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"Source": "NVD"
},
{
"Version": "3.1",
"BaseVector": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"BaseScore": 7.5,
"Source": "NVD"
}
],
"FixAvailable": "YES",
"ExploitAvailable": "NO",
"VulnerablePackages": [
{
"FilePath": "requirements.txt",
"PackageManager": "PYTHON",
"Version": "2.10",
"Epoch": "0",
"FixedInVersion": "3.7",
"Name": "idna"
},
{
"FilePath": "idna-2.10.dist-info/METADATA",
"PackageManager": "PYTHON",
"Version": "2.10",
"Epoch": "0",
"FixedInVersion": "3.7",
"Name": "idna"
}
],
"EpssScore": 4.6e-4,
"Id": "CVE-2024-3651",
"Vendor": {
"VendorCreatedAt": "2024-07-07T18:15:09.000Z",
"VendorSeverity": "HIGH",
"Url": "https://nvd.nist.gov/vuln/detail/CVE-2024-3651",
"Name": "NVD",
"VendorUpdatedAt": "2024-07-11T14:58:01.000Z"
}
}
],
"CompanyName": "Amazon",
"FindingProviderFields": {
"Types": ["Software and Configuration Checks/Vulnerabilities/CVE"],
"Severity": { "Normalized": 70, "Label": "HIGH" }
},
"ProductFields": {
"aws/inspector/ProductVersion": "2",
"aws/inspector/FindingStatus": "ACTIVE",
"aws/inspector/inspectorScore": "7.5",
"aws/securityhub/FindingId": "arn:aws:securityhub:ap-northeast-1::product/aws/inspector/arn:aws:inspector2:ap-northeast-1:012345678901:finding/c33c6e60a31f11cd71bdb927268d8afe",
"aws/securityhub/ProductName": "Inspector",
"aws/securityhub/CompanyName": "Amazon"
},
"Remediation": {
"Recommendation": {
"Text": "Remediation is available. Please refer to the Fixed version in the vulnerability details section above.For detailed remediation guidance for each of the affected packages, refer to the vulnerabilities section of the detailed finding JSON."
}
},
"SchemaVersion": "2018-10-08",
"GeneratorId": "AWSInspector",
"RecordState": "ACTIVE",
"Title": "CVE-2024-3651 - idna",
"Workflow": { "Status": "NEW" },
"Severity": { "Normalized": 70, "Label": "HIGH" },
"UpdatedAt": "2024-09-27T05:19:36.638Z",
"WorkflowState": "NEW",
"AwsAccountId": "012345678901",
"Region": "ap-northeast-1",
"Id": "arn:aws:inspector2:ap-northeast-1:012345678901:finding/c33c6e60a31f11cd71bdb927268d8afe",
"Resources": [
{
"Partition": "aws",
"Type": "AwsLambdaFunction",
"Details": {
"AwsLambdaFunction": {
"LastModified": "2024-09-27T05:19:12.000Z",
"Role": "arn:aws:iam::012345678901:role/serverlessrepo-Test-l-TestLogIngestionFunc-H98AJCXK8HB8",
"FunctionName": "test-log-ingestion",
"Runtime": "PYTHON_3_12",
"Version": "$LATEST",
"PackageType": "ZIP",
"CodeSha256": "0j3jPloHflTomYb76p1LRFpUm/hrCJ02zgI6Y24K6M0=",
"Architectures": ["X86_64"]
}
},
"Region": "ap-northeast-1",
"Id": "arn:aws:lambda:ap-northeast-1:012345678901:function:test-log-ingestion:$LATEST",
"Tags": {
"aws:cloudformation:stack-name": "serverlessrepo-Test-log-ingestion",
"serverlessrepo:semanticVersion": "2.6.4",
"lambda:createdBy": "SAM",
"aws:cloudformation:stack-id": "arn:aws:cloudformation:ap-northeast-1:012345678901:stack/serverlessrepo-Test-log-ingestion/be4da5f0-d2a5-11ed-80e2-069a21750419",
"serverlessrepo:applicationId": "arn:aws:serverlessrepo:us-east-1:123456789012:applications/Test-log-ingestion",
"aws:cloudformation:logical-id": "TestLogIngestionFunction"
}
}
],
"ProcessedAt": "2024-09-27T05:19:52.028Z"
}
]
}
}
最後に
本記事では、Amazon Inspectorの検出結果をAWS Security Hubを経由してメール通知する方法を詳細に解説しました。この設定により、以下のメリットが得られます。
- 重要なセキュリティアラートをリアルタイムで把握できる
- 通知内容をカスタマイズし、必要な情報のみを受け取れる
- セキュリティインシデントへの迅速な対応が可能になる
参考になれば幸いです。
参考










